Knowledge Creates Innovation
Knowledge Creates Innovation
 Knowledge Creates Innovation
Knowledge Creates Innovation

SASE can provide access from anywhere while being securely connected, allowing you to be confident with enterprise level security from the most untrusted remote networks. With today’s technological landscape, attack surfaces become greater and greater, but here at KCI Secure we implement a holistic approach to the security needs in every layer of your business.
Login once during your day and have access to all of your applications, like Salesforce or JIRA. Why have bookmarks when you can have one portal for all the web-based apps of your business, providing the flexibility to adapt to ever-changing needs without hindering productivity or expandability. Automation can also be used to simplify the provisioning and deployment of security and network operations.

Integrate essential functions into a cloud-native platform, simplifying IT infrastructure while enhancing security. Centrally manage, define, and enforce security policies across the network using CASB (Cloud Access Security Broker) to experience seamless, secure access for a remote workforce, and comprehensive data protection. Embrace the future of cybersecurity ensuring your business remains agile, scalable, and resilient against evolving cyber threats.
With products like data loss protection, be confident data is not in the hands of the wrong person with our integrated platform that consolidates multiple security and networking functions.
Provides secure internet access for users by inspecting and filtering web traffic for malicious content, malware, and phishing attempts.
Monitors and secures access from a centralized control location; enforcing security policies, encrypting data, and detecting unauthorized access and/or data exfiltration.
Optimizes and secures network connectivity for branch offices, remote users, and cloud resources by dynamically routing traffic based on performance, security, and business policies.
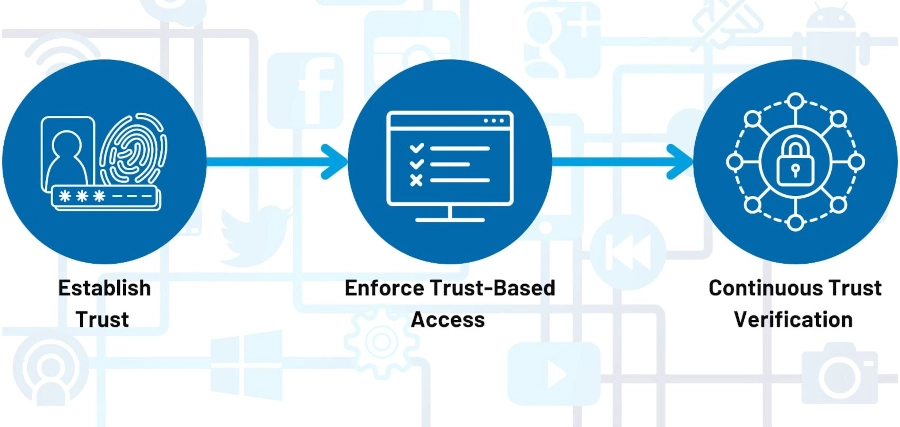
Enforces a zero-trust security model to authenticate and authorize users and devices before granting access to network resources, regardless of their location or network perimeter.
Consolidates security functions such as cloud firewall, intrusion prevention system (IPS), secure web gateway (SWG), and data loss prevention (DLP) to a single provider for simplified management and enhanced security.
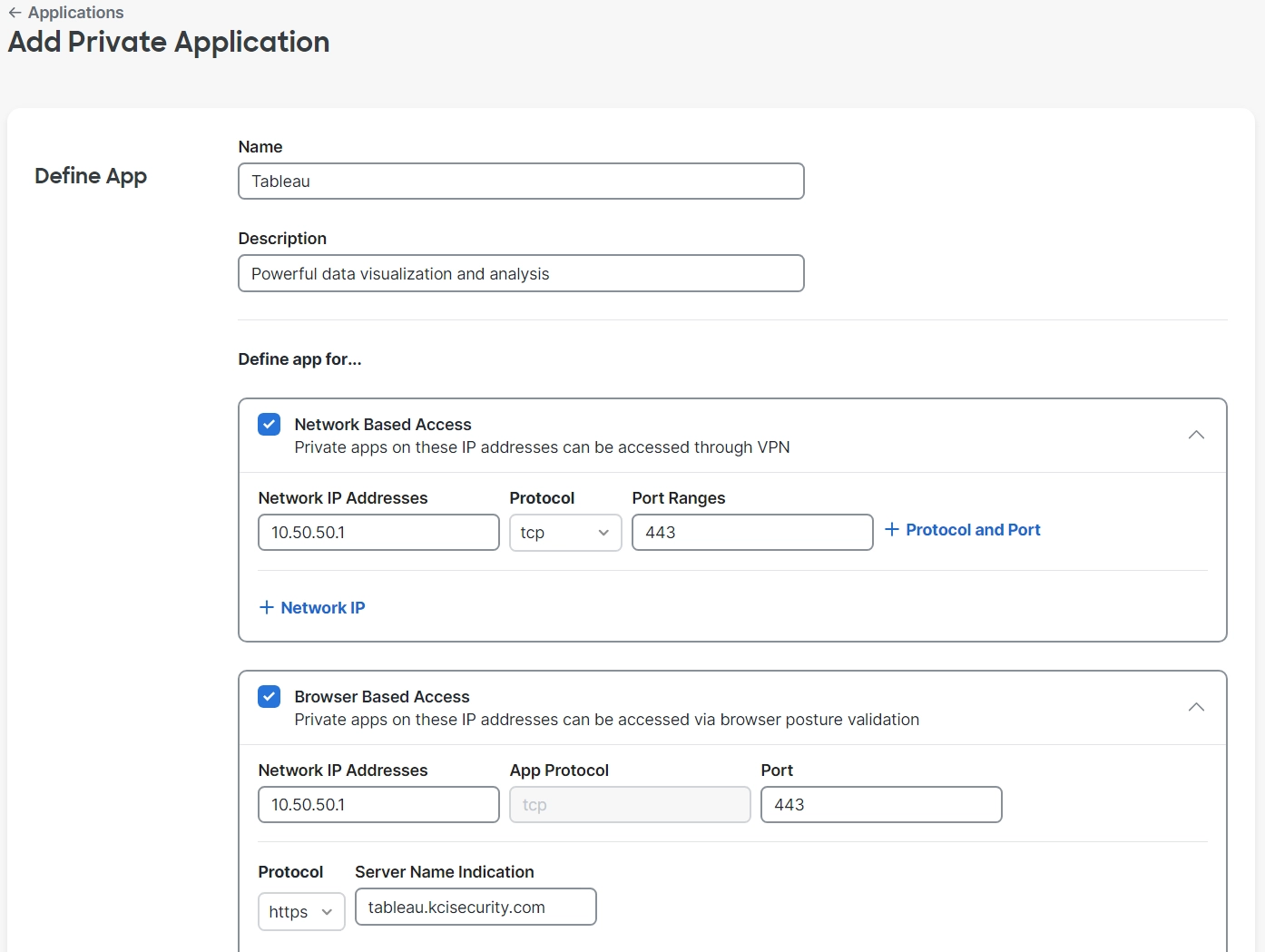
Provides secure access to corporate resources through browser based, or network-based access; while enforcing security controls and compliance requirements, and enabling access without the use of a VPN.