Knowledge Creates Innovation
Knowledge Creates Innovation
 Knowledge Creates Innovation
Knowledge Creates Innovation

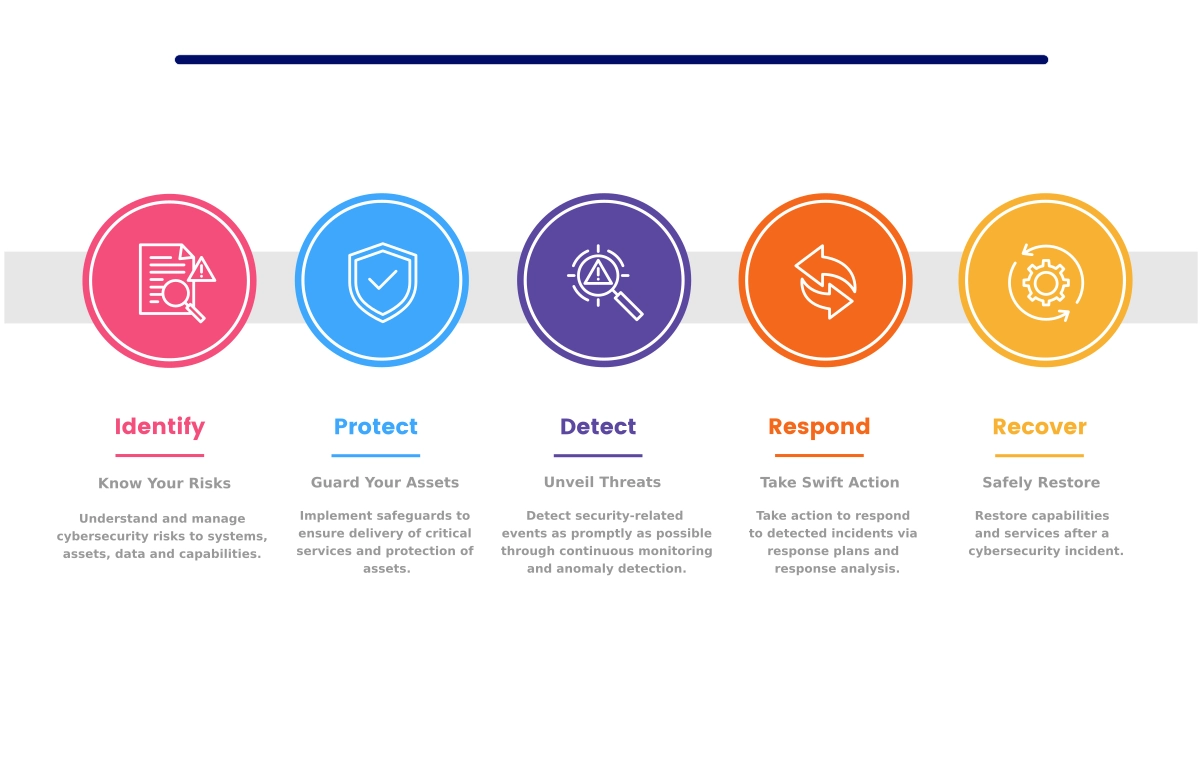
Using a combination of security and systems expertise, technology, and best practices – our services help our clients become aware and defend against the threat landscape of tomorrow.
of Organizations surveyed were breached in 2023 alone.
is the average reported time to recover from a cyber attack.
of Breaches involve the use of stolen credentials.
test