 Knowledge Creates Innovation
Knowledge Creates Innovation
 Knowledge Creates Innovation
Knowledge Creates Innovation

Our Network Audit Product offers automated data collection, customized client-facing reports, and in-depth scanning to provide a clear picture of your network’s health, performance, and security. Visualize your network structure with detailed network diagrams, analyze Active Directory configurations for optimal security, and evaluate the efficiency and reliability of cloud services. This product’s ability to identify and enable you to resolve vulnerabilities with comprehensive risk assessments will help to effectively manage your assets.
The KCI Secure Team creates a detailed list of all hardware and software components within the network; including servers, routers, switches, firewalls, and endpoints. This inventory extends to assessing your entire IT environment’s security configurations and Network Architecture. Evaluations include on-premises and cloud-based infrastructures (Active Directory, Azure, AWS) to ensure all assets are completely accounted for. By thoroughly documenting and analyzing these components, a concise picture of your IT ecosystem is established, gauging risks and enhancing overall operational efficiency.
The process of analyzing your network's layout and structure (including architecture, segmentation, and connectivity patterns) not only identifies all known devices, but also unexpected devices that may pose security risks. By thoroughly scrutinizing the network, potential vulnerabilities and rogue devices are detected, ensuring a secure and efficient network environment.
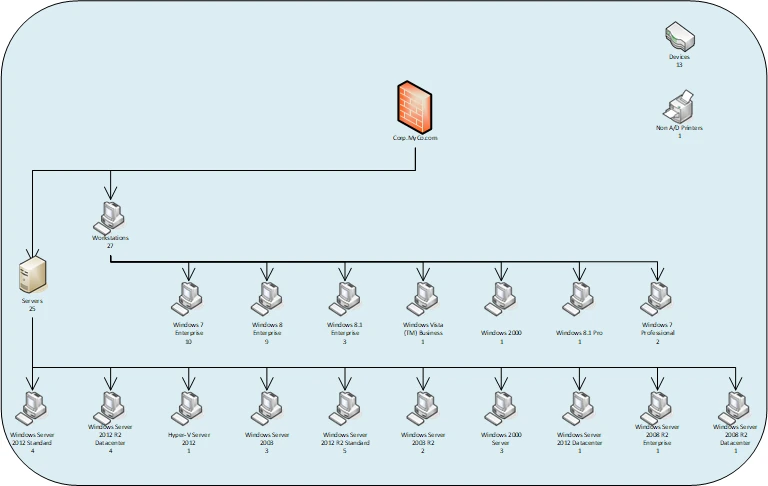
Examining the flow of data across the network is crucial for identifying patterns, trends, and potential bottlenecks. This includes leveraging port mirroring to capture and analyze traffic, as well as conducting firewall analysis to assess security rules and policies. By utilizing these methods, performance issues and security threats can be swiftly identified and addressed.
Not only will auditing your network help detect misconfigurations and vulnerabilities within its infrastructure and applications; it will also automatically assign risk scores to each identified issue, which provides a clearer understanding of their potential impact and urgency. By implementing risk scoring, organizations can prioritize remediation efforts, ensuring that the most critical security threats are addressed promptly, thereby enhancing the overall security posture and resilience of the network.
Measuring key performance indicators (like latency, throughput, and packet loss) allows for assessment of network operations and pinpoints areas for improvement. Through automated data collection and analysis, we can identify delays, data transfer constraints, and packet loss rates. This detailed evaluation provides actionable insights, enabling reliability and efficiency in the management of your network.
By analyzing audit findings and leveraging industry best practices, critical areas for improvement can be identified, allowing us to provide targeted recommendations that will enhance network performance, resilience, and security posture. At the end of an audit, a customized report is provided, detailing those recommendations to ensure an optimized network infrastructure, and fortifying against vulnerabilities while bolstering operational continuity.